
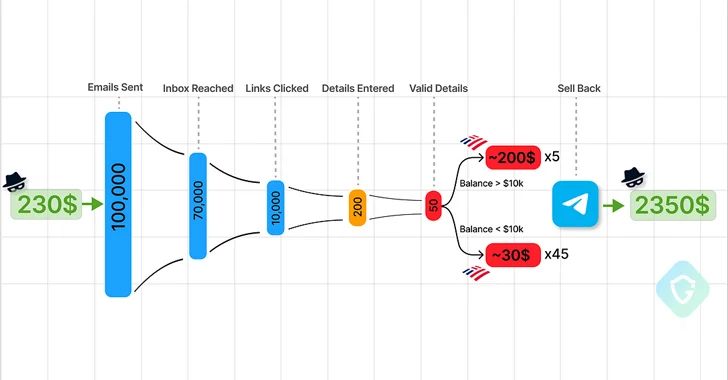
Cybersecurity researchers are calling consideration to the “democratization” of the phishing ecosystem owing to the emergence of Telegram as an epicenter for cybercrime, enabling risk actors to mount a mass assault for as little as $230.
“This messaging app has remodeled right into a bustling hub the place seasoned cybercriminals and newcomers alike change illicit instruments and insights making a darkish and well-oiled provide chain of instruments and victims’ information,” Guardio Labs researchers Oleg Zaytsev and Nati Tal mentioned in a brand new report.
“Free samples, tutorials, kits, even hackers-for-hire – every little thing wanted to assemble an entire end-to-end malicious marketing campaign.” The corporate additionally described Telegram as a “scammers paradise” and a “breeding floor for contemporary phishing operations.”
This isn’t the primary time the favored messaging platform has come below the radar for facilitating malicious actions, that are partly pushed by its lenient moderation efforts.
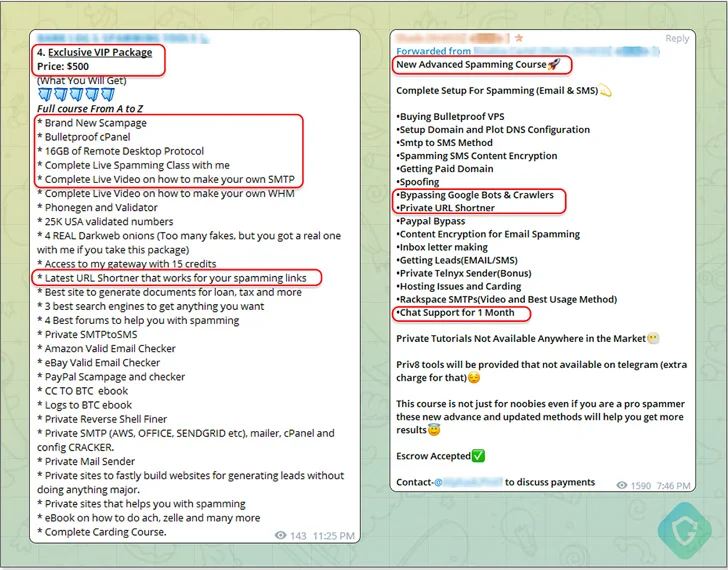
Consequently, what was once out there solely on invite-only boards in the dead of night net is now readily accessible by way of public channels and teams, thereby opening the doorways of cybercrime to aspiring and inexperienced cyber criminals.
In April 2023, Kaspersky revealed how phishers create Telegram channels to teach newbies about phishing in addition to promote bots that may automate the method of making phishing pages for harvesting delicate info reminiscent of login credentials.
One such malicious Telegram bot is Telekopye (aka Classiscam), which might craft fraudulent net pages, emails, SMS messages to assist risk actors pull off large-scale phishing scams.
Guardio mentioned the constructing blocks to assemble a phishing marketing campaign could be readily bought off Telegram – “some supplied at very low costs, and a few even free of charge” – thereby making it potential to arrange rip-off pages by way of a phishing equipment, host the web page on a compromised WordPress web site by way of an internet shell, and leverage a backdoor mailer to ship the e-mail messages.
Backdoor mailers, marketed on varied Telegram teams, are PHP scripts injected into already infected-but-legitimate web sites to ship convincing emails utilizing the reputable area of the exploited web site to bypass spam filters.
“This case highlights a twin duty for website house owners,” the researchers mentioned. “They have to safeguard not solely their enterprise pursuits but in addition defend towards their platforms being utilized by scammers for internet hosting phishing operations, sending misleading emails, and conducting different illicit actions, all unbeknownst to them.”

To additional improve the probability of success of such campaigns, digital marketplaces on Telegram additionally present what’s often called “letters,” that are “expertly designed, branded templates” that make the e-mail messages seem as genuine as potential to trick the victims into clicking on the bogus hyperlink pointing to the rip-off web page.
Telegram can also be host to bulk datasets containing legitimate and related e-mail addresses and telephone numbers to focus on. Known as “leads,” they’re generally “enriched” with private info reminiscent of names and bodily addresses to maximise the affect.
“These leads could be extremely particular, tailor-made for any area, area of interest, demographic, particular firm prospects, and extra,” the researchers mentioned. “Each piece of private info provides to the effectiveness and credibility of those assaults.”
The best way these lead lists are ready can differ from vendor to vendor. They are often procured both from cybercrime boards that promote information stolen from breached corporations or by means of sketchy web sites that urge guests to finish a faux survey as a way to win prizes.
One other essential part of those phishing campaigns is a method to monetize the collected stolen credentials by promoting them to different prison teams within the type of “logs,” netting the risk actors a 10-fold return on their funding primarily based on the variety of victims who find yourself offering legitimate particulars on the rip-off web page.
“Social media account credentials are offered for as little as a greenback, whereas banking accounts and bank cards might be offered for tons of of {dollars} — relying on their validity and funds,” the researchers mentioned.
“Sadly, with only a small funding, anybody can begin a big phishing operation, no matter prior data or connections within the prison underworld.”
