

Cybersecurity researchers have detected within the wild yet one more variant of the Phobos ransomware household often known as Faust.
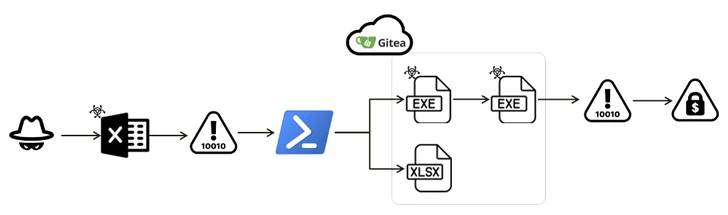
Fortinet FortiGuard Labs, which detailed the newest iteration of the ransomware, stated it is being propagated via an an infection that delivers a Microsoft Excel doc (.XLAM) containing a VBA script.
“The attackers utilized the Gitea service to retailer a number of information encoded in Base64, every carrying a malicious binary,” safety researcher Cara Lin stated in a technical report revealed final week. “When these information are injected right into a system’s reminiscence, they provoke a file encryption assault.”
Faust is the newest addition to a number of ransomware variants from the Phobos household, together with Eking, Eight, Elbie, Devos, and 8Base. It is value noting that Faust was beforehand documented by Cisco Talos in November 2023.
The cybersecurity agency described the variant as energetic since 2022 and “doesn’t goal particular industries or areas.”
The assault chain commences with an XLAM doc that, when opened, downloads Base64-encoded information from Gitea with a view to save a innocent XLSX file, whereas additionally stealthily retrieving an executable that masquerades as an updater for the AVG AntiVirus software program (“AVG updater.exe”).
The binary, for its half, capabilities as a downloader to fetch and launch one other executable named “SmartScreen Defender Home windows.exe” with a view to kick-start its encryption course of by using a fileless assault to deploy the malicious shellcode.
“The Faust variant reveals the power to take care of persistence in an surroundings and creates a number of threads for environment friendly execution,” Lin stated.
The event comes as new ransomware households resembling Albabat (aka White Bat), Kasseika, Kuiper, Mimus, and NONAME have gained traction, with the previous a Rust-based malware that is distributed within the type of fraudulent software program resembling a faux Home windows 10 digital activation software and a cheat program for the Counter-Strike 2 sport.
Trellix, which examined the Home windows, Linux, and macOS variations of Kuiper earlier this month, attributed the Golang-based ransomware to a risk actor named RobinHood, who first marketed it on underground boards in September 2023.
“The concurrency targeted nature of Golang advantages the risk actor right here, avoiding race situations and different frequent issues when coping with a number of threads, which might have in any other case been a (close to) certainty,” safety researcher Max Kersten stated.
“One other issue that the Kuiper ransomware leverages, which can also be a purpose for Golang’s elevated recognition, are the language’s cross-platform capabilities to create builds for quite a lot of platforms. This flexibility permits attackers to adapt their code with little effort, particularly for the reason that majority of the code base (i.e., encryption-related exercise) is pure Golang and requires no rewriting for a distinct platform.”
NONAME can also be noteworthy for the truth that its information leak web site imitates that of the LockBit group, elevating the likelihood that it might both be one other LockBit or that it collects leaked databases shared by LockBit on the official leak portal, researcher Rakesh Krishnan identified.
The findings observe a report from French cybersecurity firm Intrinsec that linked the nascent 3AM (additionally spelled ThreeAM) ransomware to the Royal/BlackSuit ransomware, which, in flip, emerged following the shutdown of the Conti cybercrime syndicate in Could 2022.
The hyperlinks stem from a “vital overlap” in ways and communication channels between 3 AM ransomware and the “shared infrastructure of ex-Conti-Ryuk-TrickBot nexus.”
That is not all. Ransomware actors have been noticed as soon as once more utilizing TeamViewer as an preliminary entry vector to breach goal environments and try and deploy encryptors based mostly on the LockBit ransomware builder, which leaked in September 2022.
“Risk actors search for any obtainable technique of entry to particular person endpoints to wreak havoc and presumably prolong their attain additional into the infrastructure,” cybersecurity agency Huntress stated.
In latest weeks, LockBit 3.0 has additionally been distributed within the type of Microsoft Phrase information disguised as resumes focusing on entities in South Korea, in keeping with the AhnLab Safety Intelligence Heart (ASEC).
