

Cybersecurity researchers have found an up to date variant of a stealer and malware loader known as BunnyLoader that modularizes its numerous features in addition to enable it to evade detection.
“BunnyLoader is dynamically growing malware with the aptitude to steal info, credentials and cryptocurrency, in addition to ship extra malware to its victims,” Palo Alto Networks Unit 42 stated in a report revealed final week.
The brand new model, dubbed BunnyLoader 3.0, was introduced by its developer named Participant (or Player_Bunny) on February 11, 2024, with rewritten modules for information theft, decreased payload measurement, and enhanced keylogging capabilities.
BunnyLoader was first documented by Zscaler ThreatLabz in September 2023, describing it as a malware-as-a-service (MaaS) designed to reap credentials and facilitate cryptocurrency theft. It was initially provided on a subscription foundation for $250 per 30 days.

The malware has since undergone frequent updates which are aimed toward evading antivirus defenses in addition to increasing on its information gathering features, with BunnyLoader 2.0 launched by the tip of the identical month.
The third technology of BunnyLoader goes a step additional by not solely incorporating new denial-of-service (DoS) options to mount HTTP flood assaults towards a goal URL, but in addition splitting its stealer, clipper, keylogger, and DoS modules into distinct binaries.
“Operators of BunnyLoader can select to deploy these modules or use BunnyLoader’s built-in instructions to load their alternative of malware,” Unit 42 defined.
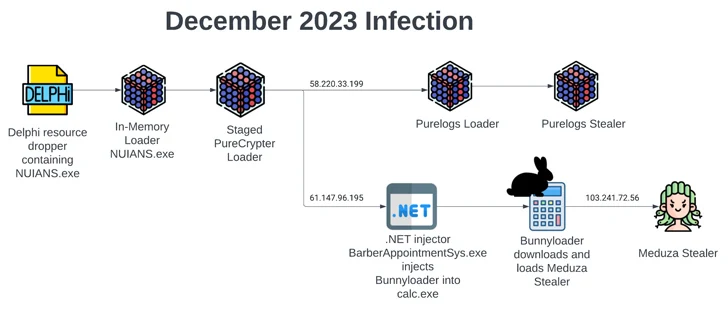
An infection chains delivering BunnyLoader have additionally grow to be progressively extra refined, leveraging a beforehand undocumented dropper to loader PureCrypter, which then forks into two separate branches.
Whereas one department launches the PureLogs loader to in the end ship the PureLogs stealer, the second assault sequence drops BunnyLoader to distribute one other stealer malware known as Meduza.
“Within the ever altering panorama of MaaS, BunnyLoader continues to evolve, demonstrating the necessity for risk actors to steadily retool to evade detection,” Unit 42 researchers stated.
The event comes amid the continued use of SmokeLoader malware (aka Dofoil or Sharik) by a suspected Russian cybercrime crew known as UAC-006 to focus on the Ukrainian authorities and monetary entities. It is recognized to be lively since 2011.
As many as 23 phishing assault waves delivering SmokeLoader had been recorded between Might and November 2023, in accordance with an exhaustive report revealed by Ukraine’s State Cyber Safety Middle (SCPC).

“Primarily a loader with added information-stealing capabilities, SmokeLoader has been linked to Russian cybercrime operations and is available on Russian cybercrime boards,” Unit 42 stated.
Including to BunnyLoader and SmokeLoader are two new info stealer malware codenamed Nikki Stealer and GlorySprout, the latter of which is developed in C++ and provided for $300 for a lifetime entry. In response to RussianPanda, the stealer is a clone of Taurus Stealer.
“A notable distinction is that GlorySprout, in contrast to Taurus Stealer, doesn’t obtain extra DLL dependencies from C2 servers,” the researcher stated. “Moreover, GlorySprout lacks the Anti-VM characteristic that’s current in Taurus Stealer.”
The findings additionally comply with the invention of a brand new variant of WhiteSnake Stealer that enables for the theft of important delicate information from compromised programs. “This new model has eliminated the string decryption code and made the code simple to know,” SonicWall stated.
