Between 2019 and December 2022, a particularly superior iMessage vulnerability was within the wild that was ultimately named “Operation Triangulation” by safety researchers at Kasperksy who found it. Now, they’ve shared all the pieces they know concerning the “most refined assault chain” they’ve “ever seen.”
In the present day on the Chaos Communication Congress, Kaspersky safety researchers Boris Larin, Leonid Bezvershenko, and Georgy Kucherin gave a presentation overlaying Operation Triangulation. This marked the primary time the three “publicly disclosed the main points of all exploits and vulnerabilities that had been used” within the superior iMessage assault.
The researchers additionally shared all of their work on the Kaspersky SecureList weblog right this moment.
The Pegasus 0-click iMessage exploit has been known as “one of the vital technically refined exploits.” And Operation Triangulation seems to be at a equally scary degree – Larin, Bezvershenko, and Kucherin have stated, “That is undoubtedly probably the most refined assault chain we’ve got ever seen.”
0-day assault chain to 0-click iMessage exploit
This vulnerability existed till iOS 16.2 was launched in December 2022.
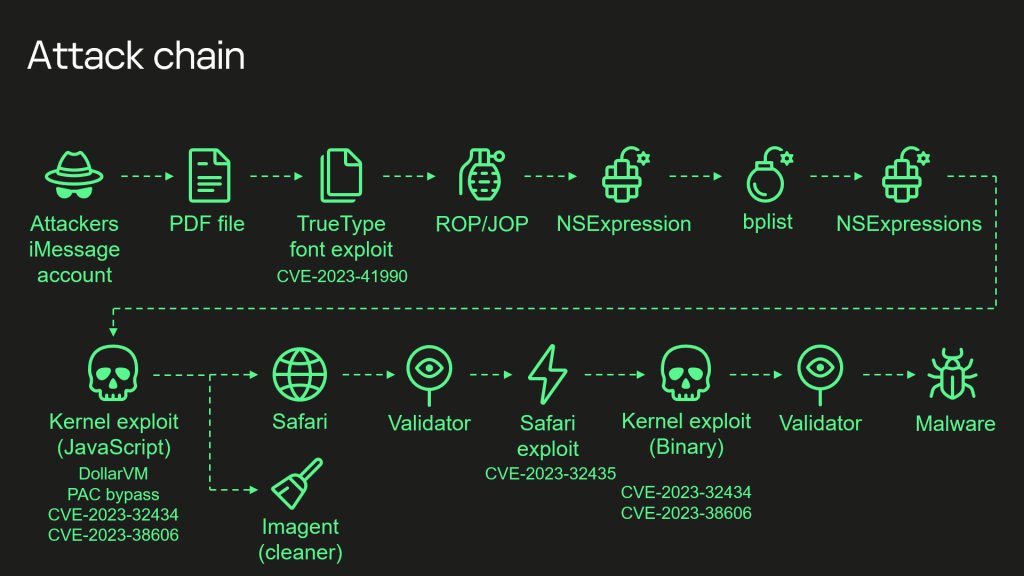
Right here’s the total complicated assault chain, together with the 4 0-days used to achieve root privileges of a sufferer’s gadget:
- Attackers ship a malicious iMessage attachment, which the appliance processes with out displaying any indicators to the person.
- This attachment exploits the distant code execution vulnerability CVE-2023-41990 within the undocumented, Apple-only ADJUST TrueType font instruction. This instruction had existed because the early nineties earlier than a patch eliminated it.
- It makes use of return/soar oriented programming and a number of phases written within the NSExpression/NSPredicate question language, patching the JavaScriptCore library atmosphere to execute a privilege escalation exploit written in JavaScript.
- This JavaScript exploit is obfuscated to make it fully unreadable and to attenuate its dimension. Nonetheless, it has round 11,000 strains of code, that are primarily devoted to JavaScriptCore and kernel reminiscence parsing and manipulation.
- It exploits the JavaScriptCore debugging characteristic DollarVM ($vm) to achieve the power to control JavaScriptCore’s reminiscence from the script and execute native API capabilities.
- It was designed to help each outdated and new iPhones and included a Pointer Authentication Code (PAC) bypass for exploitation of latest fashions.
- It makes use of the integer overflow vulnerability CVE-2023-32434 in XNU’s reminiscence mapping syscalls (mach_make_memory_entry and vm_map) to acquire learn/write entry to the complete bodily reminiscence of the gadget at person degree.
- It makes use of {hardware} memory-mapped I/O (MMIO) registers to bypass the Web page Safety Layer (PPL). This was mitigated as CVE-2023-38606.
- After exploiting all of the vulnerabilities, the JavaScript exploit can do no matter it needs to the gadget together with operating spyware and adware, however the attackers selected to: (a) launch the IMAgent course of and inject a payload that clears the exploitation artefacts from the gadget; (b) run a Safari course of in invisible mode and ahead it to an online web page with the following stage.
- The online web page has a script that verifies the sufferer and, if the checks cross, receives the following stage: the Safari exploit.
- The Safari exploit makes use of CVE-2023-32435 to execute a shellcode.
- The shellcode executes one other kernel exploit within the type of a Mach object file. It makes use of the identical vulnerabilities: CVE-2023-32434 and CVE-2023-38606. It’s also large when it comes to dimension and performance, however fully completely different from the kernel exploit written in JavaScript. Sure components associated to exploitation of the above-mentioned vulnerabilities are all that the 2 share. Nonetheless, most of its code can be devoted to parsing and manipulation of the kernel reminiscence. It comprises varied post-exploitation utilities, that are principally unused.
- The exploit obtains root privileges and proceeds to execute different phases, which load spyware and adware. We coated these phases in our earlier posts.
The researchers spotlight that they’ve nearly reverse-engineered “each side of this assault chain” and shall be publishing extra articles in 2024 going in-depth on every vulnerability and the way it was used.
However curiously, Larin, Bezvershenko, and Kucherin word there’s a thriller remaining in terms of CVE-2023-38606 that they’d like assist with.
Particularly, it’s not clear how attackers would have recognized concerning the hidden {hardware} characteristic:
We’re publishing the technical particulars, in order that different iOS safety researchers can affirm our findings and provide you with potential explanations of how the attackers discovered about this {hardware} characteristic.
In conclusion, Larin, Bezvershenko, and Kucherin say that techniques “that depend on ‘safety by means of obscurity’ can by no means be actually safe.”
If you want to contribute to the undertaking, you could find the technical particulars on the Kaspersky publish.

