
Cracked software program have been noticed infecting Apple macOS customers with a beforehand undocumented stealer malware able to harvesting system info and cryptocurrency pockets knowledge.
Kaspersky, which recognized the artifacts within the wild, mentioned they’re designed to focus on machines working macOS Ventura 13.6 and later, indicating the malware’s potential to contaminate Macs on each Intel and Apple silicon processor architectures.
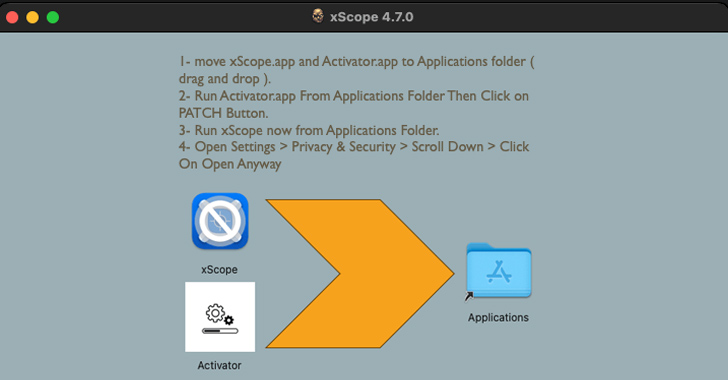
The assault chains leverage booby-trapped disk picture (DMG) recordsdata that embody a program named “Activator” and a pirated model of professional software program equivalent to xScope.
Customers who find yourself opening the DMG recordsdata are urged to maneuver each recordsdata to the Purposes folder and run the Activator element to use a supposed patch and run the xScope app.
Launching Activator, nonetheless, shows a immediate asking the sufferer to enter the system administrator password, thereby permitting it to execute a Mach-O binary with elevated permissions with a view to launch the modified xScope executable.
“The trick was that the malicious actors had taken pre-cracked software variations and added a number of bytes to the start of the executable, thus disabling it to make the person launch Activator,” safety researcher Sergey Puzan mentioned.
The subsequent stage entails establishing contact with a command-and-control (C2) server to fetch an encrypted script. The C2 URL, for its half, is constructed by combining phrases from two hard-coded lists and including a random sequence of 5 letters as a third-level area identify.

A DNS request for this area is then despatched to retrieve three DNS TXT information, every containing a Base64-encoded ciphertext fragment that’s decrypted and assembled to assemble a Python script, which, in flip, establishes persistence and capabilities as a downloader by reaching out to “apple-health[.]org” each 30 seconds to obtain and execute the primary payload.
“This was a reasonably attention-grabbing and strange manner of contacting a command-and-control server and hiding exercise inside visitors, and it assured downloading the payload, because the response message got here from the DNS server,” Puzan defined, describing it as “critically ingenious.”
The backdoor, actively maintained and up to date by the menace actor, is designed to run obtained instructions, collect system metadata, and examine for the presence of Exodus and Bitcoin Core wallets on the contaminated host.
If discovered, the functions are changed by trojanized variations downloaded from the area “apple-analyser[.]com” which can be geared up to exfiltrate the seed phrase, pockets unlock password, identify, and steadiness to an actor-controlled server.
“The ultimate payload was a backdoor that would run any scripts with administrator privileges, and change Bitcoin Core and Exodus crypto pockets functions put in on the machine with contaminated variations that stole secret restoration phrases the second the pockets was unlocked,” Puzan mentioned.
The event comes as cracked software program is more and more turning into a conduit to compromise macOS customers with a wide range of malware, together with Trojan-Proxy and ZuRu.
