
GitHub on Thursday introduced that it is enabling secret scanning push safety by default for all pushes to public repositories.
“Because of this when a supported secret is detected in any push to a public repository, you’ll have the choice to take away the key out of your commits or, when you deem the key protected, bypass the block,” Eric Tooley and Courtney Claessens mentioned.
Push safety was first piloted as an opt-in function in August 2023, though it has been beneath testing since April 2022. It turned usually accessible in Might 2023.
The key scanning function is designed to establish over 200 token varieties and patterns from greater than 180 service suppliers in an effort to stop their fraudulent use by malicious actors.
The event comes practically 5 months after the Microsoft subsidiary expanded secret scanning to incorporate validity checks for common companies resembling Amazon Internet Providers (AWS), Microsoft, Google, and Slack.
It additionally follows the invention of an ongoing “repo confusion” assault focusing on GitHub that is inundating the supply code internet hosting platform with 1000’s of repositories containing obfuscated malware able to stealing passwords and cryptocurrency from developer units.
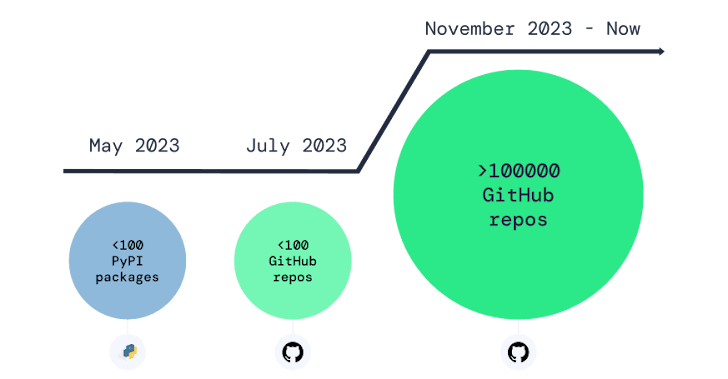
The assaults signify one other wave of the identical malware distribution marketing campaign that was disclosed by Phylum and Development Micro final yr, leveraging bogus Python packages hosted on the cloned, trojanized repositories to ship a stealer malware known as BlackCap Grabber.
“Repo confusion assaults merely depend on people to mistakenly choose the malicious model over the true one, typically using social engineering strategies as effectively,” Apiiro mentioned in a report this week.
