
GitHub on Wednesday introduced that it is making out there a function referred to as code scanning autofix in public beta for all Superior Safety clients to supply focused suggestions in an effort to keep away from introducing new safety points.
“Powered by GitHub Copilot and CodeQL, code scanning autofix covers greater than 90% of alert varieties in JavaScript, Typescript, Java, and Python, and delivers code recommendations proven to remediate greater than two-thirds of discovered vulnerabilities with little or no modifying,” GitHub’s Pierre Tempel and Eric Tooley stated.
The aptitude, first previewed in November 2023, leverages a mix of CodeQL, Copilot APIs, and OpenAI GPT-4 to generate code recommendations. The Microsoft-owned subsidiary additionally stated it plans so as to add help for extra programming languages, together with C# and Go, sooner or later.
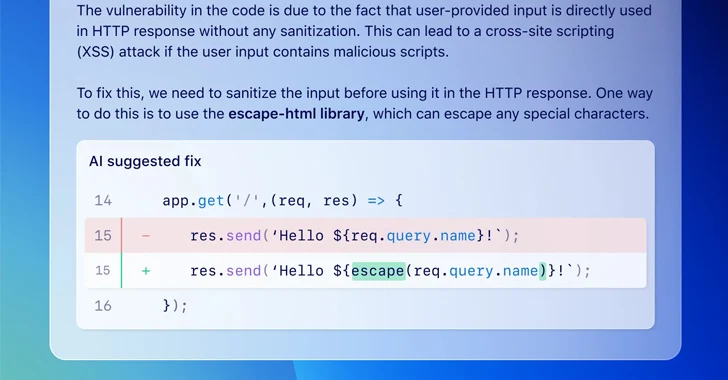
Code scanning autofix is designed to assist builders resolve vulnerabilities as they code by producing potential fixes in addition to offering a pure language rationalization when a problem is found in a supported language.

These recommendations might transcend the present file to incorporate modifications to a number of different recordsdata and the dependencies that ought to be added to rectify the issue.
“Code scanning autofix lowers the barrier of entry to builders by combining info on finest practices with particulars of the codebase and alert to counsel a possible repair to the developer,” the corporate stated.
“As a substitute of beginning with a seek for details about the vulnerability, the developer begins with a code suggestion that demonstrates a possible resolution for his or her codebase.”
That stated, it is left to the developer to judge the suggestions and decide if it is the suitable resolution and be certain that it doesn’t deviate from its meant conduct.
GitHub additionally emphasised the present limitations of the autofix code recommendations, making it crucial that builders fastidiously overview the modifications and the dependencies earlier than accepting them –
- Recommend fixes that aren’t syntactically right code modifications
- Recommend fixes which can be syntactically right code however are recommended on the incorrect location
- Recommend fixes which can be syntactically legitimate however that change the semantics of this system
- Recommend fixes that fail to handle the foundation trigger, or introduce new vulnerabilities
- Recommend fixes that solely partially resolve the underlying flaw
- Recommend unsupported or insecure dependencies
- Recommend arbitrary dependencies, resulting in potential provide chain assaults
“The system has incomplete data of the dependencies printed within the wider ecosystem,” the corporate famous. “This will result in recommendations that add a brand new dependency on malicious software program that attackers have printed underneath a statistically possible dependency title.”
