
Safety researchers have pulled the curtain again on what seems to be a variant of the notorious RustBucket malware that targets macOS methods. What was first detected earlier in April, a brand new report from Jamf Menace Labs highlights how this assault continues to evolve and who its potential targets could also be.
RustBucket is a comparatively new type of malware that particularly targets Mac customers. It’s the work of an Superior Persistent Menace (APT) group out of North Korea referred to as BlueNoroff, a sub-group of the nation-state’s well-known cybercrime enterprise Lazarus Group.
On Tuesday, Apple safety specialists at Jamf Menace Labs revealed particulars on what it believes to be a brand new later-stage macOS malware variant being tracked as ObjCShellz from BlueNoroff that intently aligns with RustBucket. “Later-stage” refers to after the preliminary an infection happens and infrequently entails information exfiltration, establishing persistence, or lateral motion inside a community.
BlueNoroff usually reaches out to potential victims below the disguise of an investor or firm head hunter, in line with Jamf. It’s additionally not unusual for risk actors to create domains that seem to belong to a respectable crypto firm to mix in with community exercise.
The invention of ObjCShellz (RustBucket-like variant) was made after Jamf researchers discovered a macOS common binary speaking with a site beforehand categorized as malicious.
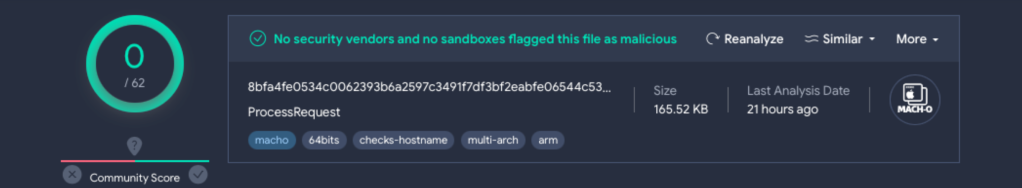
“This executable was undetected on VirusTotal on the time of our evaluation, piquing our curiosity,” Jamf said.
RustBucket compromises its targets utilizing numerous strategies, equivalent to phishing emails, malicious web sites, and drive-by downloads. As soon as contaminated, the malware communicates with command and management (C2) servers to obtain and execute numerous payloads. What’s most elusive, nonetheless, is its skill to cross by way of antivirus scanners, like VirusTotal, fully undetected.
And that’s what this new variant did.
In an try to speak with the brand new variant’s C2 server, Jamf researchers carried out a DNS pivot from the preliminary malicious area and located a number of extra URLs used for communication. In the end, they had been unsuccessful, and the C2 server instantly went offline shortly after.
“Over the previous few months, Jamf Menace Labs has uncovered numerous malware campaigns orchestrated by this elusive Superior Persistent Menace actor in an effort to steal digital belongings from victims,” Jaron Bradley, Director at Jamf Menace Labs, informed 9to5Mac.
“Our newest analysis sheds mild on a beforehand unreported piece of malware being utilized by BlueNoroff to determine covert communication channels on compromised methods. This stealthy program permits the attackers to ship and obtain information whereas the sufferer continues to make use of their pc, evading detection.”
ObjCShellz and comparable variants can pose a severe for Mac customers. Nonetheless, there are just a few methods to guard your self.
- Most significantly: Train warning when opening e mail attachments, particularly if the sender is unknown. Malware could be delivered by way of contaminated attachments.
- Make sure you’re operating the most recent model of macOS with all the safety patch goodness that comes with it. This helps with addressing identified vulnerabilities that malware can exploit.
- Set up respected antivirus and anti-malware software program in your Mac that can also detect and block malicious web sites. Whereas ObjCShellz can certainly go slip by way of undetected, it’s at all times good follow to have an additional layer of protection on Mac.
You will discover Jamf’s full report on the brand new malware variant and examine the indications of compromise right here.
