

Menace actors are leveraging digital doc publishing (DDP) websites hosted on platforms like FlipSnack, Issuu, Marq, Publuu, RelayTo, and Simplebooklet for finishing up phishing, credential harvesting, and session token theft, as soon as once more underscoring how menace actors are repurposing legit companies for malicious ends.
“Internet hosting phishing lures on DDP websites will increase the probability of a profitable phishing assault, since these websites usually have a good status, are unlikely to seem on internet filter blocklists, and will instill a false sense of safety in customers who acknowledge them as acquainted or legit,” Cisco Talos researcher Craig Jackson mentioned final week.
Whereas adversaries have used well-liked cloud-based companies resembling Google Drive, OneDrive, Dropbox, SharePoint, DocuSign, and Oneflow to host phishing paperwork up to now, the newest growth marks an escalation designed to evade e-mail safety controls.

DDP companies enable customers to add and share PDF recordsdata in a browser-based interactive flipbook format, including web page flip animations and different skeuomorphic results to any catalog, brochure, or journal.
Menace actors have been discovered to abuse the free tier or a no-cost trial interval supplied by these companies to create a number of accounts and publish malicious paperwork.
Apart from exploiting their favorable area status, the attackers benefit from the truth that DDP websites facilitate transient file internet hosting, thereby permitting revealed content material to robotically grow to be unavailable after a predefined expiration date and time.
What’s extra, productiveness options baked into DDP websites like Publuu might act as a deterrent, stopping the extraction and detection of malicious hyperlinks in phishing messages.
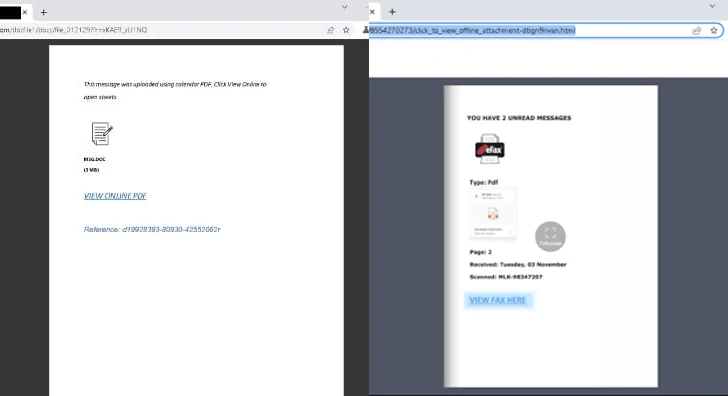
Within the incidents analyzed by Cisco Talos, DDP websites are built-in into the assault chain within the secondary or intermediate stage, sometimes by embedding a hyperlink to a doc hosted on a legit DDP website in a phishing e-mail.
The DDP-hosted doc serves as a gateway to an exterior, adversary-controlled website both immediately by clicking on a hyperlink included within the decoy file, or by way of a collection of redirects that additionally require fixing CAPTCHAs to thwart automated evaluation efforts.

The ultimate touchdown web page is a bogus website mimicking the Microsoft 365 login web page, thus permitting the attackers to steal credentials or session tokens.
“DDP websites might signify a blind spot for defenders, as a result of they’re unfamiliar to skilled customers and unlikely to be flagged by e-mail and internet content material filtering controls,” Jackson mentioned.
“DDP websites create benefits for menace actors in search of to thwart up to date phishing protections. The identical options and advantages that appeal to legit customers to those websites might be abused by menace actors to extend the efficacy of a phishing assault.”
