

Menace actors have been leveraging pretend web sites promoting widespread video conferencing software program comparable to Google Meet, Skype, and Zoom to ship quite a lot of malware concentrating on each Android and Home windows customers since December 2023.
“The risk actor is distributing Distant Entry Trojans (RATs) together with SpyNote RAT for Android platforms, and NjRAT and DCRat for Home windows programs,” Zscaler ThreatLabz researchers stated.
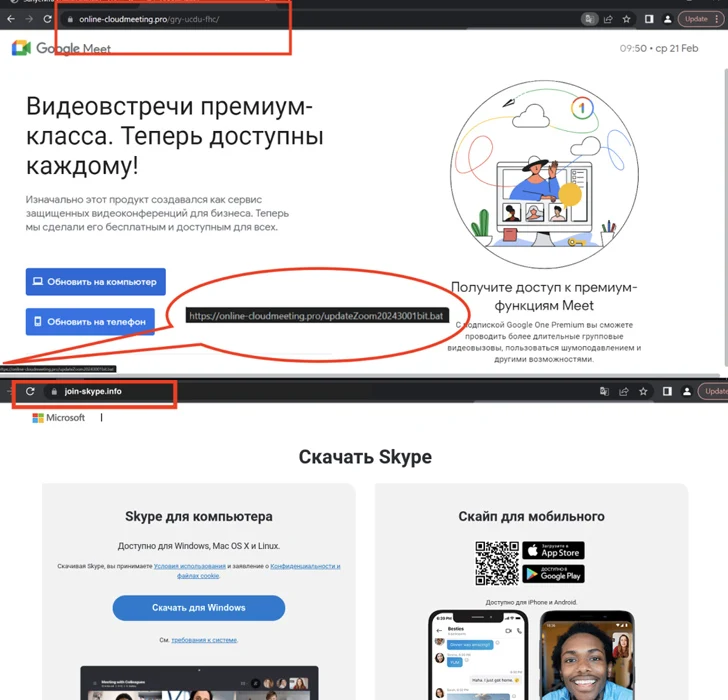
The spoofed websites are in Russian and are hosted on domains that carefully resemble their professional counterparts, indicating that the attackers are utilizing typosquatting methods to lure potential victims into downloading the malware.
Additionally they include choices to obtain the app for Android, iOS, and Home windows platforms. Whereas clicking on the button for Android downloads an APK file, clicking on the Home windows app button triggers the obtain of a batch script.
The malicious batch script is answerable for executing a PowerShell script, which, in flip, downloads and executes the distant entry trojan.
At present, there isn’t any proof that the risk actor is concentrating on iOS customers, on condition that clicking on the button for the iOS app takes the person to the professional Apple App Retailer itemizing for Skype.
“A risk actor is utilizing these lures to distribute RATs for Android and Home windows, which may steal confidential data, log keystrokes, and steal recordsdata,” the researchers stated.
The event comes because the AhnLab Safety Intelligence Middle (ASEC) revealed {that a} new malware dubbed WogRAT concentrating on each Home windows and Linux is abusing a free on-line notepad platform referred to as aNotepad as a covert vector for internet hosting and retrieving malicious code.
It is stated to be lively from a minimum of late 2022, concentrating on Asian nations like China, Hong Kong, Japan, and Singapore, amongst others. That stated, it is presently not identified how the malware is distributed within the wild.
“When WogRAT is run for the primary time, it collects fundamental data of the contaminated system and sends them to the C&C server,” ASEC stated. “The malware then helps instructions comparable to executing instructions, sending outcomes, downloading recordsdata, and importing these recordsdata.”
It additionally coincides with high-volume phishing campaigns orchestrated by a financially motivated cybercriminal actor generally known as TA4903 to steal company credentials and sure observe them with enterprise electronic mail compromise (BEC) assaults. The adversary has been lively since a minimum of 2019, with the actions intensifying publish mid-2023.
“TA4903 routinely conducts campaigns spoofing numerous U.S. authorities entities to steal company credentials,” Proofpoint stated. “The actor additionally spoofs organizations in numerous sectors together with development, finance, healthcare, meals and beverage, and others.”
Assault chains contain using QR codes (aka quishing) for credential phishing in addition to counting on the EvilProxy adversary-in-the-middle (AiTM) phishing package to bypass two-factor authentication (2FA) protections.
As soon as a goal mailbox is compromised, the risk actor has been noticed trying to find data related to funds, invoices, and financial institution data, with the final word purpose of hijacking current electronic mail threads and performing bill fraud.
Phishing campaigns have additionally functioned as a conduit for different malware households like DarkGate, Agent Tesla, and Remcos RAT, the final of which leverages steganographic decoys to drop the malware on compromised hosts.
