

Corporations are engaged in a seemingly infinite cat-and-mouse sport on the subject of cybersecurity and cyber threats. As organizations put up one defensive block after one other, malicious actors kick their sport up a notch to get round these blocks. A part of the problem is to coordinate the defensive talents of disparate safety instruments, whilst organizations have restricted assets and a dearth of expert cybersecurity consultants.
XDR, or Prolonged Detection and Response, addresses this problem. XDR platforms correlate indicators from throughout safety domains to detect threats after which present the instruments to remediate incidents.
Whereas XDR has many advantages, legacy approaches have been hampered by the shortage of good-quality knowledge. You may find yourself having an excellent view of a risk from occasions generated by your EPP/EDR system however lack occasions in regards to the community perspective (or vice versa). XDR merchandise will import knowledge from third-party sensors, however knowledge is available in totally different codecs. The XDR platform must normalize the information, which then degrades its high quality. Consequently, threats could also be incorrectly recognized or missed, or incident studies might lack the required data for fast investigation and remediation.
Cato’s Distinctive Method to Lowering Complexity
All of which makes Cato Networks’ method to XDR significantly intriguing. Introduced in January, Cato XDR is, as Cato Networks places it, the primary “SASE-based” XDR product. Safe Entry Service Edge (SASE) is an method that converges safety and networking into the cloud. SASE would appear to be a pure match for XDR as there are lots of native sensors already in a SASE platform. Gartner who outlined SASE in 2019 talks a few SASE platform together with “SD-WAN, SWG, CASB, NGFW and nil belief community entry (ZTNA)” however these are solely the required capabilities. SASE may additionally embrace superior safety capabilities similar to distant browser isolation, community sandboxing, and DNS safety. With so many native sensors already constructed into the SASE platform, you possibly can keep away from the largest downside with XDR – the shortage of excellent knowledge.
Cato SASE Cloud is the prototypical instance of what Gartner means by SASE and, on paper no less than, Cato XDR would faucet the complete energy of what SASE has to supply objective. The Cato SASE Cloud comes with a wealthy set of native sensors spanning the community and endpoint — NGFW, superior risk prevention (IPS, NGAM, and DNS Safety), SWG, CASB, DLP, ZTNA, RBI, and EPP/EDR. The latter, EPP/EDR, is simply as new as Cato XDR. Cato EPP is constructed on Bitdefender’s malware prevention know-how and shops buyer and endpoint knowledge in the identical knowledge lake as the remainder of the Cato SASE community knowledge. XDR customers find yourself with an extremely wealthy “encompass sound” view (pardon the blended metaphor) of an incident with detailed knowledge gathered from many native sensors. Cato’s capabilities are immediately on and all the time out there at scale, offering a single shared context to hunt for, detect, and reply to threats. For many who have their very own EPP/EDR options in place, Cato can work for them as properly. Cato XDR integrates with main EDR suppliers similar to Microsoft Defender, CrowdStrike, and SentinelOne.
 |
| The Cato SASE Cloud Platform structure. Cato XDR (1) faucets the various native sensors (2) constructed into the Cato SASE cloud to ship wealthy, detailed risk evaluation. All sensors run throughout all 80+ Cato PoPs worldwide, interconnected by Cato’s world non-public spine (3). Entry to the Cato SASE Cloud for websites is thru Cato’s edge SD-WAN machine, the Cato Socket (4); distant customers via the Cato Consumer or Clientless entry (5); multi-cloud deployments and cloud datacenters via Cato vSocket, Cross Join or IPsec (6); and SaaS purposes via Cato’s SaaS Optimization (7). |
Testing Atmosphere
The overview goes to deal with a day within the lifetime of a safety analyst utilizing Cato XDR. We’ll learn the way an analyst can see a snapshot of the safety threats on the community and the method for investigating and remediating them. In our situation, we have been knowledgeable of malware at 10:59 PM. We’ll examine after which remediate the incident.
It is vital to know that Cato XDR is just not offered as a standalone product, however as a part of the bigger Cato SASE Cloud. It leverages all capabilities – sensors, analytics, UI and extra – of the Cato SASE Cloud. So, to completely respect Cato XDR, one needs to be aware of the remainder of the Cato platform to finest respect the simplicity and – what Cato calls “magnificence” – of the platform. However doing so would make it troublesome, if not not possible, to have room to overview Cato XDR. We selected to take a cursory have a look at Cato general however then deal with Cato XDR. (You possibly can see a extra full albeit outdated overview of the platform from again in 2017.)
Entering into Cato XDR
As we enter the Cato SASE Cloud platform, they’re greeted with a personalized view of the enterprise community. Safety, entry, and networking capabilities can be found from pull-down menus throughout the highest and dashboards and particular capabilities for investigation, detection, and response, and practices assessments down the vertical. Accessing Cato XDR is below the Detection & Response part. To discover Cato XDR capabilities, go to Cato XDR.
 |
| Cato XDR is accessible from the left-hand aspect of the display screen (indicated by the pink field). Observe: topology proven doesn’t replicate our check setting. |
Placing Cato XDR to the Check
Clicking on the Tales Dashboard of Cato XDR offers us an general view of the tales within the enterprise (see beneath). A “story” for Cato is a correlation of occasions generated by one or a number of sensors. The story tells the narrative of a risk from its inception to decision. The very first thing we observed is that the Tales Dashboard has an intuitive and easy-to-use interface, making it easy to navigate and perceive for safety analysts of various ability ranges. We really feel that is essential for environment friendly investigations and decision-making.
To get a fast understanding of the general danger rating of the account, we appeared on the AI-powered Account Threat Rating widget. On this case, the general danger rating is 75—so, pretty excessive. This tells us we have to dig in and see what’s resulting in such a excessive rating. There are 55 incidents tales in all, 24 of that are open and 30 of that are closed.
 |
| The Cato XDR Tales Dashboard summarizes the state of tales throughout the enterprise. Throughout the highest, AI is used to guage the general danger of the account (1) with the standing of the varied tales and extra counters throughout vertical (2). |
Under the general abstract line, now we have widgets assist us perceive our tales from totally different views. The best precedence tales are sorted by an AI-powered criticality retailer (1). The rating relies on all of the story danger scores for the chosen time vary and is calculated utilizing a method developed by the Cato analysis and improvement crew. That is useful in telling us which tales needs to be addressed first. We will additionally shortly see the hosts (Prime 5 Hosts) and websites (Prime 5 Websites) concerned in essentially the most tales (2). Scrolling down we see further graphs capturing the story breakdown by criticality (3); Indicator of Assault (IoA) similar to Malware Exercise, Area Era Algorithm (DGA), and Suspicious Community Exercise (4); and MITRE ATT&CK strategies, similar to Software Layer Protocol, Exfiltration Over C2 Channel, and Automated Exfiltration Mitigation (5).
 |
| Widgets assist inform the risk story from totally different views by criticality (1), the hosts and websites concerned in essentially the most tales (2), story breakdown by criticality (3), by IoAs (4), and by Mitre ATT&CK strategies (5). |
As analysts, we wish to see which tales are open. A click on on the 24 open tales within the abstract line of the Tales Dashboard brings us to the Tales Workbench web page (additionally accessible from the navigation on the left-side of the display screen), which shows a prioritized record of all tales for environment friendly triage and higher focus. Cato makes use of an AI-powered Criticality rating to rank the tales (1). We will additionally add extra filters and slender down the record even additional to allow higher focus within the filter row (2). Grouping choices additionally allow simpler evaluation (3).
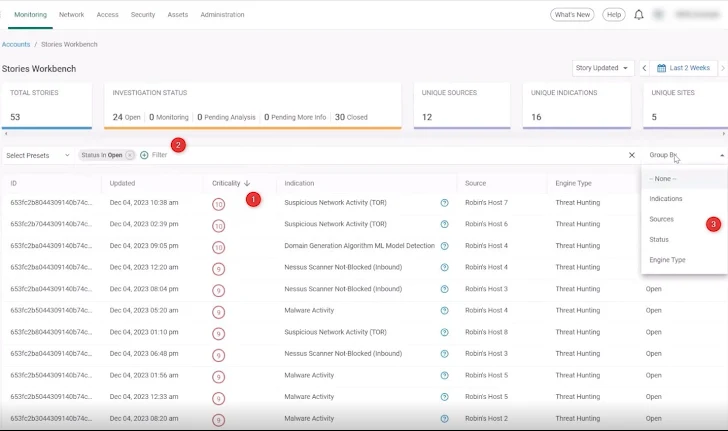 |
| The Tales Workbench lists the out there Tales, which on this case is filtered to point out the Open tales ranked by criticality (1). Additional filtering (2) and grouping (3) choices permit for environment friendly triage and investigation. |
We determined to look at the distribution of threats within the Tales Workbench display screen by grouping threats by their Distinctive Indications. Now, we will see threats by class — Malware Exercise, Suspicious Community Exercise, Area Era Algorithm (DGA), and so forth. DGA is a way utilized by malware authors to dynamically generate many domains. That is generally employed by sure sorts of malware, similar to botnets and different malicious software program, to determine communication with command-and-control servers. We went to the ultimate story at 10:59 PM and opened it for investigation.
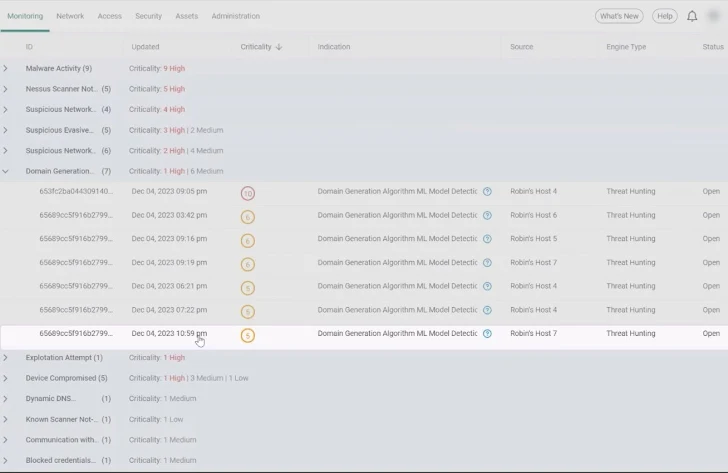 |
| The Tales Workbench display screen grouped by indications, displaying the tales with area technology algorithms (DGAs). We investigated the ultimate DGA story. |
The investigation display screen reveals a methodological course of with instruments for analyzing threats from the highest down, gaining a high-level understanding of state of affairs after which delving deeper into the investigation. First is the abstract line of the story (1). We will see that the kind of assault detected is Area Era Algorithm, that this can be a threat-hunting story, and that the variety of Related Alerts, that are the community flows that make up the story, is 26. Risk searching tales comprise correlated safety occasions and community flows and utilizing AI/ML and Risk Looking heuristics to detect elusive signatureless and zero-day threats that can’t be blocked by prevention instruments.
We will see that the story period is 9 days, indicating that we discovered Related Alerts inside a time span of 9 days, and naturally, that the standing of the story is open. Subsequent, we see the standing line, which data the actions that occurred within the story (2). At the moment, we see that the standing was “created.” Extra actions might be added as we work on the story. Shifting on to the main points, we will shortly see that the Area Era Algorithm, or DGA, was discovered on Robin’s Host 7. We see that the assault path is outbound, and the AI-powered criticality rating is 5.
 |
| The investigation display screen offers all the main points an analyst wants to analyze the story. Right here we’re seeing the opening a part of the display screen with additional element beneath. The main points of the story are summarized above (1) with actions which have been taken to remediate the incident beneath (2). This line might be up to date because the investigation progresses. |
For an easy-to-read understanding of the story, we will click on on the “See Abstract” button. Cato’s Gen AI engine summarizes the outcomes of the display screen in easy-to-read textual content. Particulars embrace the kind of communication, the IP supply, the targets, why the story was detected, and if any actions had been taken robotically, similar to blocking the site visitors.
 |
| Clicking on the “Story Abstract” button (1) generates a textual abstract of the display screen utilizing Cato’s Gen AI engine. |
Closing the Story Abstract and staying on the investigation display screen, we achieve further insights in regards to the story. Cato’s machine learning-powered Predicted Verdict analyzes the varied indicators within the story and based mostly on earlier data offers an anticipated verdict (1). One other sensible perception is the “Comparable Tales,” which can be powered by AI and, when related, will hyperlink to tales with comparable traits. There’s additionally the Playbook Information Base (highlighted) to information us on the best way to examine tales of Malicious Goal Communication.
On the proper aspect of the display screen, we will see the supply particulars (2): the IP, the OS, and the consumer. We see that this can be a Tor browser, which could be suspicious. Tor is an internet browser particularly designed for privateness and anonymity, and attackers usually use it to hide their id and exercise on-line.
We will see the assault geolocation supply (3), which communicates with totally different international locations on totally different components of the map. This will also be suspicious. Subsequent, we have a look at the Goal Actions field (4) the place we will see actions that relate to each goal concerned on this story. Since this can be a threat-hunting story, we will see a correlation between a broad set of indicators.
 |
| The investigation display screen offers additional particulars in regards to the story. Comparable tales (1) point out relates tales within the account (none are current on this case). Particulars in regards to the supply of the assault are proven (2), together with the geolocation (3). The actions associated to the goal are additionally proven (4). |
Scrolling down we look at the assault distribution timeline. We will see right here that the communication to the targets has been occurring for 9 days.
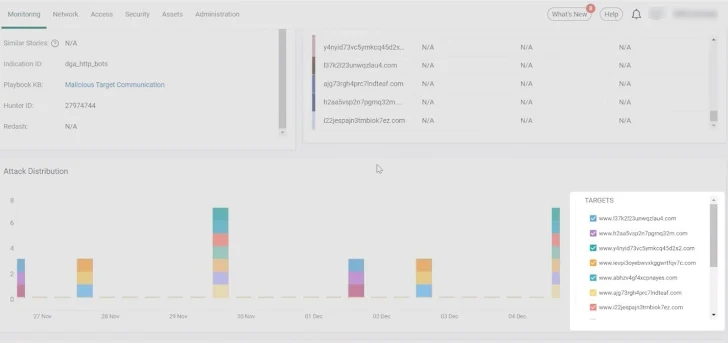 |
| The assault distribution timeline offers a chronological record of the assaults on the varied targets. Clicking on the targets permits analysts so as to add or take away them from the graphic to higher see the assault sample. |
By filtering out among the targets, we will see patterns of communications, that are simply observable. We clearly see a periodic exercise that’s indicative of bot- or script- initiated communication. Below the assault timeline, the Targets desk (1) offers further particulars in regards to the targets, together with their IPs, domains, and associated risk intelligence. The targets are sorted by malicious rating. It is a sensible rating powered by AI and ML that takes all of Cato’s risk intelligence sources, each proprietary and third occasion, and calculates the rating between zero and one to point whether or not the IP is taken into account extremely malicious or not.
 |
| Eradicating all however 4 of the targets present a periodic communication sample, which is indicative of a bot or script. Under the assault distribution timelines is the Targets desk with intensive details about the targets within the investigation. |
The recognition column reveals if the IP is “in style” or “unpopular” as decided by Cato’s proprietary algorithm measuring how usually an IP or area is visited based on Cato inner knowledge. Unpopular IPs or domains are sometimes indicative of suspicious IPs or domains. We will achieve exterior risk intelligence details about the goal by clicking third-party risk intelligence hyperlinks similar to VirusTotal, WhoIs, and AbusePDB.
 |
| Exterior risk intelligence sources are only a click on away from inside the Targets desk. |
Scrolling all the way down to the Assault Associated Flows desk, we will view extra granular particulars in regards to the uncooked community flows that compose the story, similar to the beginning time of the site visitors and the supply and vacation spot ports. On this explicit case, the vacation spot ports are unusually excessive (9001) and fewer frequent, which raises a pink flag.
Documenting What We Discovered with Cato
Let’s summarize our findings from our check case. We discovered suspicious community exercise associated to area technology algorithm that makes use of the Tor consumer. The IP has low reputation, excessive malicious scoring, and the communication follows a particular sample in distinct instances. So, we will now attain a conclusion. We suspect that there’s a malware put in on the supply endpoint, Robin’s Host 7, and that it is making an attempt to speak outdoors utilizing Tor infrastructure.
Now let’s arrange the decision within the display screen beneath. We’ll classify the story as malicious. The analyst severity could be medium. The sort is anonymizer. We will see the main points within the picture beneath. The classification could be DGA. Then we will save the decision on this incident story.
 |
| The safety analyst can doc a verdict to assist others perceive the risk. |
As soon as saved, we will see that that opening risk searching display screen has been up to date. The second row now reveals that the analyst has set the severity to Medium, and the decision is ready to malicious. Now the response could be to mitigate the risk by configuring a firewall rule.
 |
| The up to date Detection & Response story now displays that the analyst has taken motion. The severity is ready to “Medium” with a verdict of “Malicious” and kind has been modified to “Anonymizer.” Beneath we not solely see that the story was created (1) however that the analyst set severity to “medium” (2) and the Verdict has been set to “Malicious.” |
Mitigate The Risk with Cato
Usually, analysts would wish to leap to a different platform to take motion, however within the case of Cato it could all be achieved proper within the XDR platform. A block rule could be simply created in Cato’s Web firewall to forestall the unfold of the malware. We copy the goal area that seems within the assault community flows, add the area to the App/Class part of the firewall rule, and hit apply. Worldwide the DGA area is now blocked.
 |
| The up to date Cato firewall display screen with the rule blocking entry to the DGA-generated area. |
Conclusion
With its introduction of SASE-based XDR, Cato Networks promised to vastly simplify risk detection, incident response, and endpoint safety. They seem to uphold the promise. The check case situation we ran via above ought to take an skilled safety analyst lower than 20 minutes from begin to mitigation. And that was with no setup time or implementation or knowledge assortment efforts. The info was already there within the knowledge lake of the SASE platform.
Cato Networks has efficiently prolonged the safety companies of its unified networking and safety platform with XDR and associated options. It is a large profit for patrons who’re decided to up their sport on the subject of risk detection and response. Need to be taught extra about Cato XDR? Go to the Cato XDR web page.
