
Risk actors have been noticed leveraging a now-patched safety flaw in Microsoft Home windows to deploy an open-source data stealer known as Phemedrone Stealer.
“Phemedrone targets internet browsers and knowledge from cryptocurrency wallets and messaging apps akin to Telegram, Steam, and Discord,” Pattern Micro researchers Peter Girnus, Aliakbar Zahravi, and Simon Zuckerbraun mentioned.
“It additionally takes screenshots and gathers system data concerning {hardware}, location, and working system particulars. The stolen knowledge is then despatched to the attackers by way of Telegram or their command-and-control (C&C) server.”
The assaults leverage CVE-2023-36025 (CVSS rating: 8.8), a safety bypass vulnerability in Home windows SmartScreen, that could possibly be exploited by tricking a person into clicking on a specifically crafted Web Shortcut (.URL) or a hyperlink pointing to an Web Shortcut file.
The actively-exploited shortcoming was addressed by Microsoft as a part of its November 2023 Patch Tuesday updates.
The an infection course of entails the menace actor internet hosting malicious Web Shortcut recordsdata on Discord or cloud companies like FileTransfer.io, with the hyperlinks additionally masked utilizing URL shorteners akin to Quick URL.
The execution of the booby-trapped .URL file permits it to hook up with an actor-controlled server and execute a management panel (.CPL) file in a fashion that circumvents Home windows Defender SmartScreen by profiting from CVE-2023-36025.
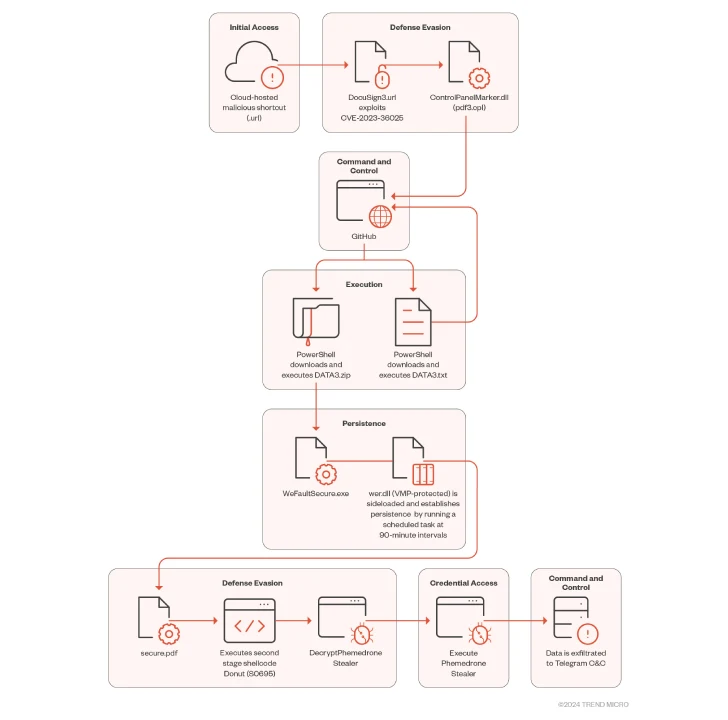
“When the malicious .CPL file is executed by way of the Home windows Management Panel course of binary, it in flip calls rundll32.exe to execute the DLL,” the researchers mentioned. “This malicious DLL acts as a loader that then calls on Home windows PowerShell to obtain and execute the subsequent stage of the assault, hosted on GitHub.”
The follow-on payload is a PowerShell loader (“DATA3.txt”) that acts as a launchpad for Donut, an open-source shellcode loader that decrypts and executes Phemedrone Stealer.
Written in C#, Phemedrone Stealer is actively maintained by its builders on GitHub and Telegram, facilitating the theft of delicate data from compromised programs.
The event is as soon as once more an indication that menace actors are getting more and more versatile and shortly adapting their assault chains to capitalize on newly disclosed exploits and inflict most injury.
“Regardless of having been patched, menace actors proceed to seek out methods to take advantage of CVE-2023-36025 and evade Home windows Defender SmartScreen protections to contaminate customers with a plethora of malware sorts, together with ransomware and stealers like Phemedrone Stealer,” the researchers mentioned.
